Secure DevOps Kit for Azure (AzSK) is packed with great set of tools, scripts and tasks to help you scan your Azure resources for security issues. At my client we have scheduled this as part of CICD to scan resources and generate report. The extension also includes a task to scan your ARM templates for security issues - The benefit is that you can STOP security issues even before they get deployed to Azure, ensuring you always do secured resource deployment. In this post we will see how easy it is to include this task in your CICD pipeline to scan for issues in your ARM templates.
The first thing to do, if you have not done already is, to go to VS Marketplace and install the extension
-
We will be testing our ARM templates as soon as we commit to the source control. So lets create a build definition mapped to our ARM template repository.
-
Next add the
AzSK ARM Template Checkertask to the build pipeline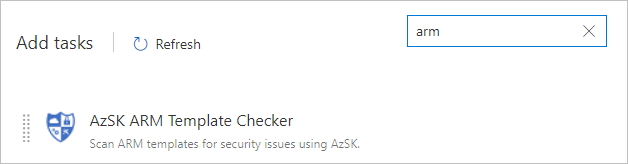
-
Next, configure the task - To start scanning, you just need to provide the root folder where you have ARM templates (and optionally mark it to scan recursively).
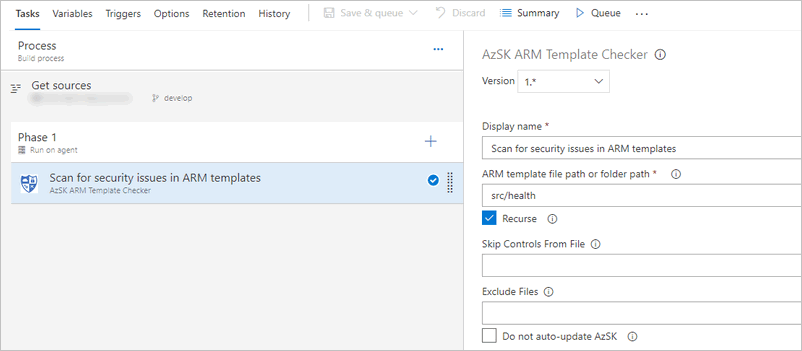
-
Run the build and let the build complete. You will see glimpse of the scan in the build output itself.
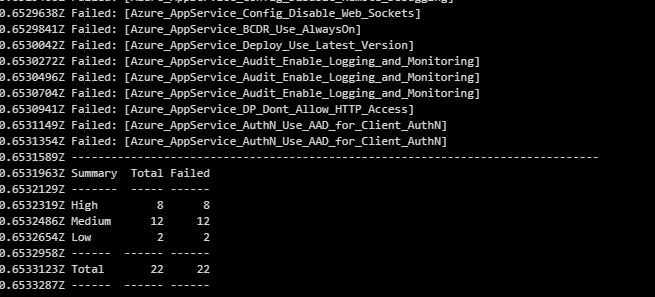
-
Once the build completes, you will find that task has attached all the results to the build log. You will be surprised to see the issues you find in your ARM templates.
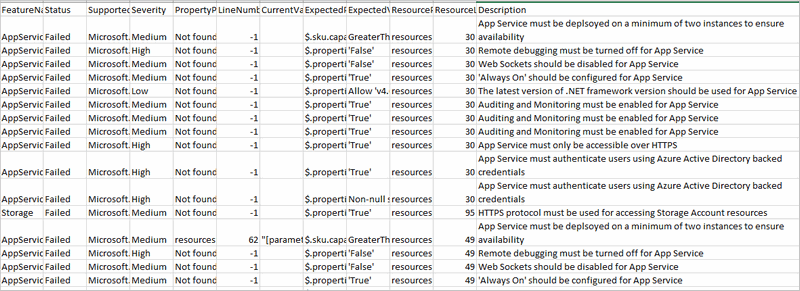
Occasionally you will find issues which you have decided as safe to ignore. The task allows you to skip such failures from the scan so that you will not get alerted as a security issue or cause in build failures.
The way you configure this is simple - Use the generated csv file and keep only entries you need to ignore from the scan and commit to your repository as a csv file. Then specify this file in the task as below.
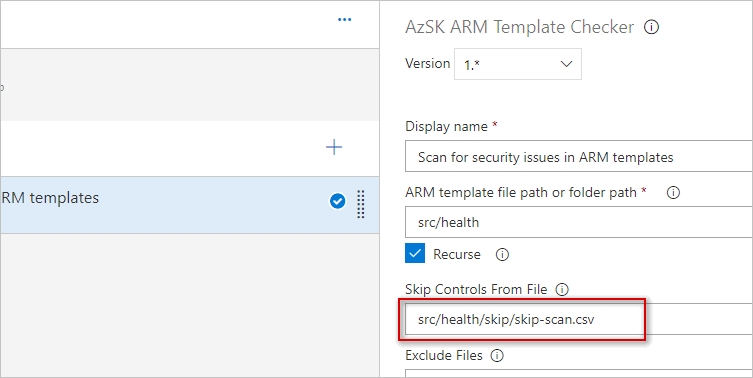
The task currently scans App Service, Storage, SQL, CDN, Traffic Manager, Document DB, Redis Cache, and Data Lake services only.
That’s it for now. Hope you found this post useful.